If you’re not a pretty serious gadgeteer, this post isn’t for you. Nothing to see here; move along…
The intersection of hardware and software has always been an interesting place, even more so when security engineering is involved.
I recently bought a Rigol DS1074Z oscilloscope. It’s a neat gadget and I’m really pleased with it.
Digression: for those who haven’t used an oscilloscope before, they’re handy gadgets for understanding what’s going on in a circuit. Most people have used a voltmeter at some point. Oscilloscopes measure voltage too, but do so in a way that lets you see how a voltage is changing as time passes. The result is a graph on the oscilloscope screen, with voltage on the Y axis and time on the X axis. Modern digital oscilloscopes also generally let you measure more than one voltage at the same time (my scope is a four-channel scope, so it can handle four simultaneous measurements). Digital storage oscilloscopes provide additional tools for understanding and analyzing signals, but underneath all the complexity it’s just measuring how input voltages behave over time.
For a long time, oscilloscopes have been costly. It’s been difficult to purchase something useful for less than about $2,000, and 4-channel scopes have been much more expensive than that. But pricing has changed in recent years. Founded in 1998, Rigol is a relative newcomer to the test equipment scene that has turned out some cleverly-designed and very capable gear. The DS1074Z, Rigol’s entry-level 4-channel scope, provides 70 MHz of input bandwidth and costs just $585. The DS1104Z offers 100 MHz of input bandwidth and sells for $830.
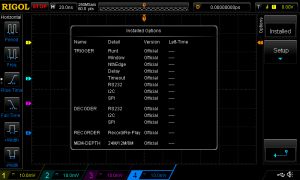
Like a lot of newer digital storage oscilloscopes, the Rigol DS1074Z supports some optional capabilities (additional storage memory, extra signal analysis modes, etc.) The capabilities are present on every oscilloscope and can be unlocked with a code provided by the manufacturer.
Securing this process is challenging for an equipment manufacturer, especially if you happen to make things like oscilloscopes that are used by curious, technically-inclined users.
The forums associated with David L. Jones’ excellent EEVblog site have been abuzz for a long time with discussion about the internals of these scopes.
Research into the option keys revealed that they’re a digitally signed version of the scope’s serial number plus an option code. Elliptic-curve cryptography is used to generate the signature.
From a security perspective, this is a good choice. The use of a public-key cryptosystem means that it shouldn’t be possible to figure out how to generate working option keys even given access to all of the data stored within the oscilloscope. And ECC keys are fairly short, which is important when the user has to enter keys, Ouija-board style, into the scope in order to turn on an option.
Rigol’s ECC key length is 56 bits, meaning it would take 2^56 (4,722,366,482,869,645,213,696) tries to try every possible key. On average, you’d find the key in half that time, but 2,361,183,241,434,822,606,848 is still quite a few times to have to try something! If you could try one trillion combinations per second, it would still take 35+ years, on average, to brute-force the key.
Rigol used a widely-available ECC library (MIRACL) for their implementation. This is a good thing; implementing crypto yourself is almost always a bad idea. But they didn’t read (or understand) the documentation, with the result that they made some fundamental mistakes in their crypto implementation. The consequences? Their generated keys had an effective length of about 14 bits. That means that it would require, at worst, 2^14 (16,384) tries to brute-force the signing key (and half that on average).
So it turns out to be easier for the determined hobbyist to add options to the DS1074Z that would otherwise add over $650 to the price of the scope.
But that’s not all, as it turns out! The hardware for the scope with 70 MHz input bandwidth and the hardware for the 100 MHz version turns out to be identical; it’s possible to convert the DS1074Z into the DS1104Z with another option code. So for those keeping score, it’s become possible to start with a $585 oscilloscope and wind up with capabilities that would cost $1,515 to obtain.
Rigol’s response to this has been interesting. They’re clearly aware of the hacks and have taken some halfhearted measures in their most recent equipment (the DS2xxxA series) to make user feature enablement a little bit harder. But they haven’t shown any signs of starting an arms race over this. My guess is that they figured, correctly, that they weren’t really losing sales as a result of the option hacks. It seems unlikely that many corporate/institutional purchasers would try to generate and load their own unsupported option codes onto an oscilloscope. But because they’re still relatively easy to hack, the Rigol scopes have become an even better value for the electronics hobbyist .
This isn’t the only hackable thing I’ve played with recently. More on another piece of test gear (and a very different manufacturer response) in a subsequent posting…